Firefox reports "The certificate is not trusted because it was issued by an invalid CA certificate". While other browser like ie and chrome has no problem
Firefox reports "The certificate is not trusted because it was issued by an invalid CA certificate" (Error code: sec_error_untrusted_issuer)
Senario : Proxy intercepts HTTPS. We have deployed internal Enterprise CA and proxy is also a intermedeate CA. Hence browsers shouldn't have any certificate validation problem. Other browsers like ie and chrome works fine. Adding exception is not a final soltuion.
Opaite Mbohovái (10)
I'm a little confused by your statement that your proxy server is also an intermediate CA. If you look at the certificate on IE or Chrome and follow the chain up to the trusted root, is your proxy somehow filling the gap??
hi jscher2000, You are right. The proxy is subordinate CA of Enterprise root CA. So that certificate issued by proxy doesn't break the certificate chain. All PCs has root CA certificates pushed by AD, because Proxy is subordinate CA of Root CA, the certificates issued by Proxy can be validated by Root CA certificate on the PC.
This works good for my ie and chrome.
The certificate viewer on Firefox shows the certificate hierarchy correctly
What does it say under the Technical Details?
Does Firefox show the full chain if you inspect the certificate?
Check out why the site is untrusted (click "Technical Details to expand that section) and if this is caused by a missing intermediate certificate then see if you can install this intermediate certificate from another source.
You can retrieve the certificate and check details like who issued certificates and expiration dates of certificates.
- Click the link at the bottom of the error page: "I Understand the Risks"
Let Firefox retrieve the certificate: "Add Exception" -> "Get Certificate".
- Click the "View..." button and inspect the certificate and check who is the issuer.
You can see more Details like intermediate certificates that are used in the Details pane.
Below is what it says under Technical details
Technical Details
www.google.com uses an invalid security certificate.
The certificate is not trusted because the issuer certificate is not trusted. (Error code: sec_error_untrusted_issuer)
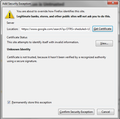
Add Security Exception says " The certificate is not trusted, because it hasn't be verified by recognized authority using a secure signature" (image attached)
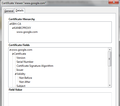
Firefox shows full chain (find attached image)
Question is: if there is any issue with certificate or chain, how is it working for ie and chrome ?
The real problem for me is Firefox is just saying the certificate is not trusted. It is not giving any troubleshooting details/ or i don't know where to look for troubleshooting data.
Moambuepyre
What do you see when you inspect the certificate chain in another browser (e.g. Google Chrome)?
Firefox doesn't link the KBH-CA to a built-in certificate and this is causing the error message.
Who is the issuer of the KBH-CA certificate?
Response to the quries as below :- What do you see when you inspect the certificate chain in another browser (e.g. Google Chrome)?
Answer : Certificate chain is valid and not broken
Firefox doesn't link the KBH-CA to a built-in certificate and this is causing the error message.
Answer : What is "built-in certificate" ?
Who is the issuer of the KBH-CA certificate?
Answer: As mentioned already it an Internal Enterprise CA. KBH-CA is root CA. Hence there are no issuer for KBH-CA.
None of the answers are helpful. I am attempting to log into a military site that uses a CAC certificate for authentication. I added all the exceptions I could find to allow this link to load but Firefox cuts in and tells me the page requires a client certificate (installed and works with Chrome, IE). Your client certificate features are not working correctly.
I have the same issue but with a site called www.faxzero.com. After entering the information it believes that the site is not trusted. I don't have the problem with www.google.com though.
Hi mace2
Could you please keep the discussion in your own thread as this thread is about a different issue than yours.
You have a problem with a different missing intermediate certificate (PositiveSSL CA 2).
Moambuepyre