import cer certificate for email signature verification
Hello,
I want to verify the digital signature of an email. The email sender has released a certificate .cer http://www.ros.ie/devcentre/email-certificate.html
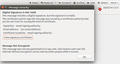
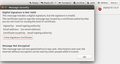
I read help pages like https://support.mozilla.org/en-US/kb/signatures https://support.mozilla.org/en-US/kb/configuring-certificates and tried to import the certificate in Preferences > Certificates > View certificates but I could not get the email verification working. When I open the email, I see an error icon (red cross over an envelope). The error message is "Digital Signature is not valid" (see attached).
It seems there is a problem with the Certificate Authority but I can not find one and I can not figure how to trust this certificate or how to relate it to email signature verification.
Thank you for reading.
ჩასწორების თარიღი:
ყველა პასუხი (6)
See http://kb.mozillazine.org/Installing_an_SMIME_certificate
And there is no attachment.
ჩასწორების თარიღი:
I think your problem here is that it appears to be a self-signed certificate, and as such, your computer has no basis to trust it.
There are discussions about setting exceptions for such certificates, usually in the context of visiting a particular website. I don't know how to translate this into the email context. And always there'll be dark warnings about why you should think long and hard before trusting it. How sure can you be it is really from who says it's from? That's the whole point of CA's; they have a reputation to protect so we can trust them.
Sorry, no simple answer (from me at least).
Hmm, that article http://kb.mozillazine.org/Installing_an_SMIME_certificate seems to suggest that what you needed was the .cer file, which you now have. Hmm…
christ1 said
See http://kb.mozillazine.org/Installing_an_SMIME_certificate And there is no attachment.
Hello,
Thanks for the link. I added the attachment to the question (sorry about that). I followed the instructions in "Other people's certificates" http://kb.mozillazine.org/Installing_an_SMIME_certificate
before you can import an SMIME certificate that is issued by an unrecognized CA or is self-signed, you must first acquire and import the certificate for the issuing CA. In the case of a self-signed certificate, you will need to acquire a ".cer" file from the individual whose certificate you wish to add
I suppose that it is the .cer from http://www.ros.ie/devcentre/email-certificate.html
a copy of their SMIME certificate as a ".cer" file. You can import it into your "Authorities" tab.
I did that and got a pop-up "Alert" saying "This is not a certificate authority certificate, so it can't be imported into the certificate authority list.".
I will contact the issuer and ask them for the CA certificate.
you will be able to send encrypted messages to the email address in that certificate
That's not exactly what I want to do, I just want to verify a signature for an email.
Note that I set a master password for Thunderbird and restarted Thunderbird and tested again after that.
I also double clicked the certificate in my file navigator and "imported" the certificate but that did not change anything.
The email sender has released a certificate .cer http://www.ros.ie/devcentre/email-certificate.html
Quoting from the site:
You will need to install the ROS certificate in order to view signed emails without receiving security warnings. Just click on the link below to install the certificate.
This is where the trouble starts. The cert offered is supposed to be the cert of the Root CA issuing email certificates. But the cert doesn't have the 'CA' flag set, so technically it isn't allowed to issue other certs in the first place. And the lack of the 'CA' flag prevents Thunderbird from importing it as a CA cert into the 'Authorities' tab.
I also double clicked the certificate in my file navigator and "imported" the certificate but that did not change anything.
You possibly can import the cert used to sign the actual message into the Thunderbird certificate store. However, the full certification path cannot be verified due to the lack of the corresponding Root CA cert, and hence the signature verification fails.
Note that I set a master password for Thunderbird and restarted Thunderbird and tested again after that.
The master password is irrelevant here, as no private keys are involved.
ჩასწორების თარიღი:
Where do I start.
The Certificate is self signed. So for it to be trusted the issuing authority must be added as a certifying authority. Unfortunately a CER file does not cut the mustard for doing that
The certificate uses SHA1... about as useless as nothing. See here for a fairly non technical over view
The certificate length is 1024 bytes. Tohttps://www.globalsign.com/en-au/ssl-information-center/choosing-safe-key-sizes/ on that topic "As a result of this, since January 2011, Certificate Authorities have aimed to comply with NIST (National Institute of Standards and Technology) recommendations, by ensuring all new RSA certificates have keys of 2048 bits in length or longer. GlobalSign was one of the first Certificate Authorities to implement 2048 bit key strength within its Root CA Certificates, back in 1998 and other Certification Authorities have since followed suit based on these new requirements."
So like most government departments the world over they have the bull by the horns and really don't understand what they are doing, or what is best practice.
Interestingly they managed to get a real SSL certificate for their secure web site from Comodo. They also do real email certificates. https://www.enterprisessl.com/ssl-certificate-products/addsupport/secure-email-certificates.html?track=2225&key5sk1=cecd6b1338db7e8006d984643db5fe3a7350f8af
Basically I think your might try getting some real security in your revenue office. I really wonder if they are capable of managing the data they have.