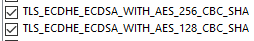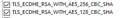I am an IT admin, after migrating our Exchange from 2010 to 2016 OWA wont open in fire fox, get Error code: NS_ERROR_NET_INADEQUATE_SECURITY
Just upgraded from Exchange 2010 to Exchange 2016, now OWA in Exchange 2016 will not open in Firefox or Chrome, it will open in IE and Microsoft Edge.
Here is the error I get in FireFox:
Your connection is not secure
The website tried to negotiate an inadequate level of security.
my.domain.com uses security technology that is outdated and vulnerable to attack. An attacker could easily reveal information which you thought to be safe. The website administrator will need to fix the server first before you can visit the site.
Error code: NS_ERROR_NET_INADEQUATE_SECURITY
I have google this for 2 days now and have double check all SSL certs, permission settings etc, and I don't know how to fix this, if anyone has any ideas I would love to hear them. Thanks John
Vahaolana nofidina
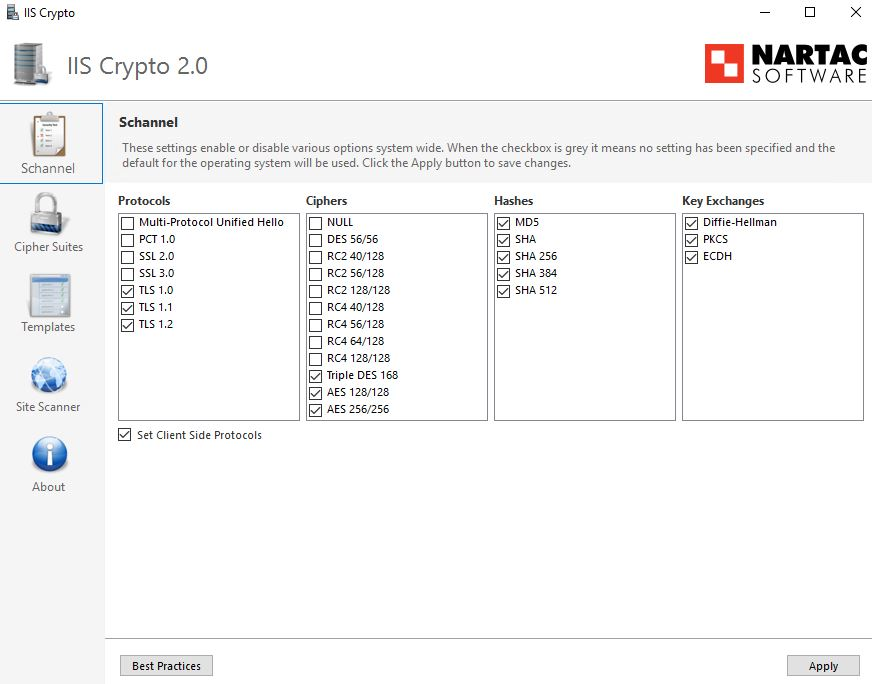
Well all fixed. I download and ran the IIS Crypto 2 tool, Clicked the best Practices button. it re-checked and uncheck boxes in each column, I hit apply, rebooted and all is fixed.
thank you so much for all you help,
John
Hamaky an'ity valiny ity @ sehatra 👍 4All Replies (13)
hi, this error code indicates your server is initiating a HTTP/2 connection but an invalid TLS configuration is detected by the browser (i'm not sure if ie/edge are supporting http/2). most likely this won't be an issue with your certificate but the server setup and cypher suites that are in use to facilitate the encrypted connection. without knowing the site in question it will be difficult to give any direct clues about what is going wrong though...
my site is:
hopefully we can hide this URL as I don't want the whole world looking at our email site.
John
Novain'i AJZ t@
thanks, so when you run the site through an analytics tool like https://www.ssllabs.com/ssltest/analyze.html you get the following results for modern browsers:
Server negotiated HTTP/2 with blacklisted suite
so i think the easiest way to work around that would be to switch off http/2 support on your server or else read up on the cipher suite requirements it would have: https://security.stackexchange.com/questions/126775/understanding-blacklisted-ciphers-for-http2 https://tools.ietf.org/html/rfc7540#appendix-A
Well thats all new to me. I will have to look in to what and how, dont want to make any drastic changes as email is working fine right now.
Yes I now see on the site it is using HTTP/2
So I guess Firefox does not support HTTP/2
Thanks, John
Novain'i AJZ t@
johnzapf said
So I guess firefox does not support http2
Firefox recently starting supporting HTTP/2 and it has stricter requirements than HTTP/1.1. You can set Firefox NOT to use HTTP/2 as a temporary workaround if necessary, but it would be a huge pain to have to have all your users do this.
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button promising to be careful.
(2) In the search box above the list, type or paste http2 and pause while the list is filtered
(3) Double-click the network.http.spdy.enabled.http2 preference to switch it from true to false
Ok, so its defiantly something to do with HTTP/2
when disabled: etwork.http.spdy.enabled.http2 preference to switch it from true to false
site works fine in Firefox.
But like you said I am not going to do this in everyones browser so I need to figure out how to fix this in IIS 10/Exchange 2016
John
Chrome 54 has a different way of describing the problem, but it seems to be the same issue:
This site can’t be reached
The webpage at https://mail.yoursite.com/owa might be temporarily down or it may have moved permanently to a new web address.
ERR_SPDY_INADEQUATE_TRANSPORT_SECURITY
Can you enable these ciphers on IIS/10? These are in order of Firefox 49's preference:
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
There's some performance-related discussion in this thread: Perfect Cipher Suite order for IIS 10 | Qualys Community
yes, same problem in chrome. IE and Windows Edge are the only browsers working.
I will start googleing on the ciphers?
John
The GCM ciphers should work with HTTP/2. It's just a puzzle of where you set that in IIS/Windows.
I just look tat this, https://msdn.microsoft.com/en-us/library/windows/desktop/mt490158(v=vs.85).aspx
show the default TLS Cipher Suites in windows Server 2016 and Windows 10 and it looks like there all there by default.
But just finding out how to check now?
Just ran this SCAN, at the bottom of the page, very nice, tells it all, but now still how to fix
https://www.nartac.com/Products/IISCrypto
Very nice tool. just dont know if I want to make these changes. Doing a backup right now before I do anything.
John
Novain'i AJZ t@
Vahaolana Nofidina
Well all fixed. I download and ran the IIS Crypto 2 tool, Clicked the best Practices button. it re-checked and uncheck boxes in each column, I hit apply, rebooted and all is fixed.
thank you so much for all you help,
John
Hey guys,
So I came across this thread yesterday after installing a new exchange server and being unable to access the ECP or OWA through FF. The kicker is, I had already run the IIS Crypto Tool as part of my server hardening process.
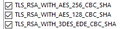
After a bit of playing around, I figured out that FF has now removed all support for SHA1 Ciphers. So you need to disable the following on the server to get it working again.
I have added in the 3DES as it is now being considered fundamentally weak and has been considered replaced by AES. You can leave these off if you want.