How to fix 'SEC_ERROR_UNKNOWN_ISSUER' I am unable to open google.com. FF V.58.0.2. Pls let me know a firefox ver that allows google to be added as exception.
Your connection is not secure
The owner of google.com has configured their website improperly. To protect your information from being stolen, Firefox has not connected to this website.
This site uses HTTP Strict Transport Security (HSTS) to specify that Firefox may only connect to it securely. As a result, it is not possible to add an exception for this certificate.
google.com uses an invalid security certificate. The certificate is not trusted because the issuer certificate is unknown. The server might not be sending the appropriate intermediate certificates. An additional root certificate may need to be imported. Error code: SEC_ERROR_UNKNOWN_ISSUER
Peer’s Certificate issuer is not recognized.
HTTP Strict Transport Security: false HTTP Public Key Pinning: true
Certificate chain:
ప్రత్యుత్తరాలన్నీ (3)
Google instructs browsers not to allow exceptions ("strict transport security"). However, we usually can help you identify the source of the issue.
Is this issue only on Google, or on numerous HTTPS pages?
If only Google, you may be able to inspect the certificate as follows:
(1) Copy/paste this internal address to the address bar and press Enter to load it:
chrome://pippki/content/exceptionDialog.xul
(2) Enter https://www.google.com/ into Location and click Get Certificate
(3) Click the View button to pop up the problem certificate, and check the Issued by section -- I'm attaching a screenshot for comparison.
What does yours show?
@Jscher2000,
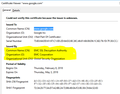
Thanks for your quick response, this is not only with Google but many other https pages too. I tried the above you mentioned and below attached is the screenshot for your reference.
Even after confirming the security exception using this method I am unable to load Google page.
Please help!
Hi skb1, thanks for the screenshot.
I think the EMC certificate is associated with a filtering product used in business networks. Does this problem occur only at work?
Could you check whether you get the same "man in the middle" on Google in Internet Explorer 11?
If you can confirm that this is in fact a correct, appropriate, and trustworthy device/service to be reading all of your internet traffic, here are two workarounds to get Firefox to trust all of the fake certificates it will generate:
Option #1: Import the Signing Certificate
If you import the EMC signing certificate into Firefox's certificate store, then all of its fake certificates will be trusted.
(A) If you do not already have a certificate file ready to import, you can export it from IE or Chrome.
- This may appear in IE's Certificates dialog OR it may appear when you view the certificate details on any secure page you load in IE/chrome
- The Export or Copy to file button starts the Export Wizard. Use the DER format and save to a convenient location
Example screenshots: https://support.mozilla.org/questions/1199797#answer-1064849
(B) When finished with all the necessary exports to complete the chain in the Certification Path, you can import the certificates into the Firefox Authorities tab:
- Windows: "3-bar" menu button (or Tools menu) > Options
- Mac: "3-bar" menu button (or Firefox menu) > Preferences
- Linux: "3-bar" menu button (or Edit menu) > Preferences
- Any system: type or paste about:preferences into the address bar and press Enter/Return to load it
In the search box at the top of the page, type cert and Firefox should filter the list. Click "View Certificates" to open the Certificate Manager and click the "Authorities" tab. Then you can use the "Import" button to import the proxy server's certificate.
(Fourth and fifth screenshots in the above-linked post.)
When asked, I suggest allowing the certificate for websites only unless your IT suggests otherwise.
It's a bit of pain, but the advantage of that approach is that you are making the minimal compromise of security.
Option #2: Trust all Signing Certificates in the Windows Cert Store
(A) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button promising to be careful.
(B) In the search box above the list, type or paste root and pause while the list is filtered
(C) Double-click the security.enterprise_roots.enabled preference to switch the value from false to true
I'm not sure whether that will start working immediately or after the next time to exit Firefox and start it up again. I guess you'll know if you visit an HTTPS address and Firefox no longer objects.
The disadvantage of this method is that any security compromise of the system certificate store will affect Firefox, too.