Potential security risk message incorrect
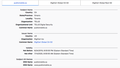
From my public IP of 104.158.49.18 FF ses the web site https://www.publicmobile.ca/ as a potential security risk. FF is reporting this incorrectly as other web browsers show this site as valid. I have included the certificate values.
what is the reason for the error meesage? Someone could be trying to impersonate the site and you should not continue.
Websites prove their identity via certificates. Firefox does not trust www.publicmobile.ca because its certificate issuer is unknown, the certificate is self-signed, or the server is not sending the correct intermediate certificates.
Error code: SEC_ERROR_UNKNOWN_ISSUER
วิธีแก้ปัญหาที่เลือก
If you click through to view the certificate from the taskbar, it shows the chain at the top of the cert window. Clicking each will show the referenced cert.
When using ssllabs.com, if you click one of the server addresses and scroll to the bottom of the report, it will also show you the chain and what is missing, if anything.
อ่านคำตอบนี้ในบริบท 👍 0การตอบกลับทั้งหมด (19)
There is security software like Avast, Kaspersky, BitDefender and ESET that intercept secure connection certificates and send their own.
https://support.mozilla.org/en-US/kb/firefox-cant-load-websites-other-browsers-can
https://support.mozilla.org/en-US/kb/firefox-and-other-browsers-cant-load-websites
https://support.mozilla.org/en-US/kb/secure-connection-failed-error-message
https://support.mozilla.org/en-US/kb/connection-untrusted-error-message
Websites don't load - troubleshoot and fix error messages
http://kb.mozillazine.org/Error_loading_websites
What do the security warning codes mean
- MOZILLA_PKIX_ERROR_MITM_DETECTED
- uses an invalid security certificate SSL_ERROR_BAD_CERT_DOMAIN
- configured their website improperly
How to troubleshoot the error code "SEC_ERROR_UNKNOWN_ISSUER" on secure websites https://support.mozilla.org/en-US/kb/troubleshoot-SEC_ERROR_UNKNOWN_ISSUER
The invalid cert message is occuring on linux as well as Mac OS.
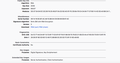
I have enclosed a clearer publicmobile.ca cert
This works for me on Linux.
There are two IP addresses for this domain if I test the server.
The first address seems to be OK with no issues reported apart missing SNI support and only support for a few acceptable cipher suites (most are considered weak).
The second server is more problematic:
This server doesn't send required intermediate certificates (DigiCert Global CA G2) needed to build a certificate chain that ends in a trusted root certificate, so if you end up on this server then you get an error in case Firefox hasn't cached the missing intermediate certificate.
Strangely Firefox message appears and disappears for this site. Below the fingerprint for the certificate is a match but it still occasionally gives that message
https://www.grc.com/fingerprints.htm publicmobile.ca publicmobile.ca — 29:26:5F:8E:5D:60:12:46:FC:B9:B6:3C:DE:5D:7C:8F:51:6D:A9:65
It probably depends on to which server you are routed at the time, as noted above by cor-el.
I would not expect the certificate SHA finger print to match.The certificate shows the correct Hash value verified by GRC.com server.
My DNS servers from Vmedia inc are 198.251.50.199 and 198.251.50.200 If one is resolving incorrectly I would expect the sha1 hash not to be correct but it is correct.
From https://www.grc.com/fingerprints.htm
publicmobile.ca publicmobile.ca — 29:26:5F:8E:5D:60:12:46:FC:B9:B6:3C:DE:5D:7C:8F:51:6D:A9:65
Here is the error and the certificate.
Peer’s Certificate issuer is not recognized.
HTTP Strict Transport Security: false HTTP Public Key Pinning: false
Certificate chain:
BEGIN CERTIFICATE-----
MIIGQDCCBSigAwIBAgIQBhoW3r+sph64BMbbButhrDANBgkqhkiG9w0BAQsFADBE MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMR4wHAYDVQQDExVE aWdpQ2VydCBHbG9iYWwgQ0EgRzIwHhcNMTkwNjI1MDAwMDAwWhcNMjAwNzE0MTIw MDAwWjB8MQswCQYDVQQGEwJDQTEQMA4GA1UECBMHT250YXJpbzEQMA4GA1UEBxMH VG9yb250bzEOMAwGA1UEChMFVEVMVVMxHzAdBgNVBAsTFlRFTFVTIERpZ2l0YWwg U2VjdXJpdHkxGDAWBgNVBAMTD3B1YmxpY21vYmlsZS5jYTCCASIwDQYJKoZIhvcN AQEBBQADggEPADCCAQoCggEBAN03OpTsLtgWJUvvCtKSrQ/+y4r5yjqEcTewFE09 oLgqdNu4VdbtYhqz6m9aDl84T2ayuDHShAnH1lbyge18KrpyLSiV/OoPTonyfSz/ vXtBZFvWj4Mzse5SoSwYPYU84bQAlHd7+Ca1i2FzT+WPkaG64iKMWc9l453rGdY9 sDTVFC/8s7318pCS1hnrsg8yVxBLTeJiUmpoXqojH32I/qlAbrCfpWmPUh0OGDXa trqYeXkAUuLIs8bNsdxk+ktr7qj3NiHmDPfXQ1V7JhoXLU9cuCDofT0O9sXd+AMP W3uvOkABnCietlIjbE9zn2nJ3XYwLesH2Fsq8BhPWCMMuu0CAwEAAaOCAvQwggLw MB8GA1UdIwQYMBaAFCRuKy3QapJRUSVpAaqaR6aJ50AgMB0GA1UdDgQWBBSLRroi hBjrWV86Z4+zJ7LPL9OMPTAvBgNVHREEKDAmgg9wdWJsaWNtb2JpbGUuY2GCE3d3 dy5wdWJsaWNtb2JpbGUuY2EwDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsG AQUFBwMBBggrBgEFBQcDAjB3BgNVHR8EcDBuMDWgM6Axhi9odHRwOi8vY3JsMy5k aWdpY2VydC5jb20vRGlnaUNlcnRHbG9iYWxDQUcyLmNybDA1oDOgMYYvaHR0cDov L2NybDQuZGlnaWNlcnQuY29tL0RpZ2lDZXJ0R2xvYmFsQ0FHMi5jcmwwTAYDVR0g BEUwQzA3BglghkgBhv1sAQEwKjAoBggrBgEFBQcCARYcaHR0cHM6Ly93d3cuZGln aWNlcnQuY29tL0NQUzAIBgZngQwBAgIwdAYIKwYBBQUHAQEEaDBmMCQGCCsGAQUF BzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20wPgYIKwYBBQUHMAKGMmh0dHA6 Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2VydEdsb2JhbENBRzIuY3J0MAkG A1UdEwQCMAAwggEEBgorBgEEAdZ5AgQCBIH1BIHyAPAAdgC72d+8H4pxtZOUI5eq kntHOFeVCqtS6BqQlmQ2jh7RhQAAAWuPlcUGAAAEAwBHMEUCIFoy+lqHcXoA/G1L /ABlCT8sZvFVNaho4nQPlHgyuwY0AiEAw1GA0rE46JII/QkMsZtI+9IRgJDP28Gh fG8SgjxXYW4AdgBep3P531bA57U2SH3QSeAyepGaDIShEhKEGHWWgXFFWAAAAWuP lcRUAAAEAwBHMEUCIQCP50aMvaWx/eFIzqZPOEHtiJnyUVtQJhix91ERxVhwowIg HufqsqQwFjiOsBmFt7a20MUetUAG7osXxVQyX1AEkmEwDQYJKoZIhvcNAQELBQAD ggEBAIayRDVOHvBau4RTm2RrPGqrDKGSX1agk4g4NE6BeXcjLE1OfOA15xv3Gqqs g0ArAdM4B5KAF+JFVleFZmWEmKQq5KBr1mkV8QYlxhHmnZ5L1F2snP2LKMF0YQST nhO0xEGgMEZWNioNj4B+gDFpPnZzk8f0BhWhfLlcvp4WFt9Qt9lASrhpuoCikfCG lgYTc42w9UE9Z1DjV+KanUx4cc4G0GpWT1faF3GnziwfjP1/xDZ75iwMCDTQ4gcU K4r1JZYhRBsoeHf8HNgfxMAA8mND16OHJh9IEhpgX9ZY/ipyhJ6djNRcnsIJE/sn myplE2T+1TqLSbGSZstx4Qyd8js=
END CERTIFICATE-----
It isn't resolving incorrectly, there are 2 IP addresses to which the domain name can resolve. Both have incomplete certificate chains while i am looking right now. The intermediate certificate is available to download, but Firefox doesn't look for these. The cert should be sent by the server.
; <<>> DiG 9.11.3-1ubuntu1.11-Ubuntu <<>> www.publicmobile.ca ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23760 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;www.publicmobile.ca. IN A ;; ANSWER SECTION: www.publicmobile.ca. 300 IN A 54.83.51.244 www.publicmobile.ca. 300 IN A 23.23.153.163
The certificate you are looking at is fine, the fingerprints would match. The problem is not with that certificate, but with the trust chain. The server should simply send the intermediate cert.
https://support.mozilla.org/en-US/kb/error-codes-secure-websites#w_missing-intermediate-certificate
That being said, it has obviously sent the intermediate certificates sometimes, because i can load the site. Last time from IP 23.23.153.163
GEThttps://publicmobile.ca/en/bc/ [HTTP/1.1 200 OK 366ms] Connection: Host publicmobile.ca: HTTP Strict Transport Security: Disabled Public Key Pinning: Disabled Certificate: Issued To Common Name (CN): publicmobile.ca Organization (O): TELUS Organizational Unit (OU): <Not Available> Issued By Common Name (CN): DigiCert Global CA G2 Organization (O): DigiCert Inc Organizational Unit (OU): <Not Available> Period of Validity Begins On: June 24, 2019 Expires On: July 14, 2020
DigiCert Global CA G2 is the intermediate, therefore i don't get the warning and i connect.
Just for flavor, the site has other errors, such as they are trying to embed a Google Map but they haven't had their site URL authorized for using the API.
If the site had any contact info, i would contact them. Their forum doesn't even have a subforum for site issues, and i am personally not poking them on social media or their generic whois mail address. (domain.registration[arobase]telus [dot]com)
Thanks. Crankygoat.
the command GEThttps://publicmobile.ca/en/bc/ I beilieve you ran from dig command. I get a different display
dig GEThttps://publicmobile.ca/en/bc/
- <<>> DiG 9.10.6 <<>> GEThttps://publicmobile.ca/en/bc/
- global options: +cmd
- Got answer:
- ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 28372
- flags: qr rd ra ad; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
- OPT PSEUDOSECTION:
- EDNS: version: 0, flags:; udp: 512
- QUESTION SECTION:
- GEThttps://publicmobile.ca/en/bc/. IN A
- AUTHORITY SECTION:
. 3338 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2020011600 1800 900 604800 86400
- Query time: 436 msec
- SERVER: 9.9.9.9#53(9.9.9.9)
- WHEN: Thu Jan 16 04:16:39 EST 2020
- MSG SIZE rcvd: 137
GEThttps://publicmobile.ca/en/bc/ (etc.) was the entry i got looking at the Web Console after the page had loaded. I just used that to see to which of the IP addresses i was routed when loading the page in a browser.
You are going to get NXDOMAIN (domain doesn't exist) from dig or nslookup as GEThttps://publicmobile.ca/en/bc/ is not a domain. publicmobile.ca and www.publicmobile.ca are valid domains.
If i had a decent way to contact them, i would just tell them to test their certs and see that their intermediate cert is not (or not always) sent, which causes the connection to fail in Firefox.
I just tried again and today i am sent to the 54.83.51.24 address.
I have no idea why i have gotten certificates and you have not, especially considering different cert tests say the intermediate is not sent. (Maybe i got it in a box of Cracker Jack?) I get the same results with FF 71 and 73.
Yes. I understand I did enter the incorrect domain. However I noticed that Safari browser as well as my Android Firefox never seems to get the certificate error message and both are functioning on the same network.
I will have to perform more testing to see if this is just coincidence.
I believe the problem may be with my ISP Vmedia.ca I cannot ping any known IP for Vmedia.ca such as 151.139.128.10 or their DNS servers 198.251.50.199 or 198.251.50.200.
IP address 104.158.49.18 Hostname 18.49.158.104.in-addr.arpa IP Address Location Country Canada (CA) State/Region Ontario (ON) City Hamilton ISP ViaNetTV Inc ASN 54198 Timezone America/Toronto Local Time Fri, 17 Jan 2020 00:20:23 -0500 Latitude/Longitude 43.2284,-79.9071
traceroutes to vmedia.ca my ISP gives me
traceroute 151.139.128.10
traceroute to 151.139.128.10 (151.139.128.10), 64 hops max, 52 byte packets
1 2 3 3.52.251.198.in-addr.arpa (198.251.52.3) 366.954 ms * 423.370 ms 4 198.251.49.89 (198.251.49.89) 307.191 ms 191.471 ms 126.917 ms 5 198.251.51.56 (198.251.51.56) 54.088 ms 28.712 ms 28.767 ms 6 198.251.50.16 (198.251.50.16) 36.279 ms 59.615 ms 25.908 ms 7 be4582.211.ccr32.yyz02.atlas.cogentco.com (38.122.70.217) 22.520 ms 23.665 ms 48.061 ms 8 be3529.rcr51.b054249-0.yyz02.atlas.cogentco.com (154.54.24.194) 135.003 ms 22.556 ms 22.233 ms 9 * * *
10 * * * 11 * * * 12 * * *
Line 4 is Cogent a different ISP. So from my workstation to directly to Vmedia.ca I am going thorugh cogent 154.54.24.194.
Try to rename the cert9.db file (cert9OLD.db) and remove the previously used cert8.db file in the Firefox profile folder with Firefox closed to remove intermediate certificates and exceptions that Firefox has cached.
If this has helped to solve the problem then you can remove the renamed cert9OLD.db file. Otherwise you can undo the rename and restore cert9.db.
You can use the button on the "Help -> Troubleshooting Information" (about:support) page to go to the current Firefox profile folder or use the about:profiles page.
- Help -> Troubleshooting Information -> Profile Folder/Directory:
Windows: Show Folder; Linux: Open Directory; Mac: Show in Finder - https://support.mozilla.org/en-US/kb/Profiles
I did not modify the cert8.db I reinstalled 72 and the certificate message disappeared. However the Ubuntu workstation still has the certificat error which suggests an induced certificate error with Firefox.
On the original workstation without with the certificate error FF produced the error occassionaly but Safari on the same workstation never produced the certificate error. Also https://www.ssllabs.com grades the site as B, so I do not know what FF is stating when it whos the certificate error. FF on my android which is version 68.4.1 does not produce the error.
As noted, when the intermediate certificate is not sent, Firefox has a problem with it. Other browsers will search for an intermediate cert and download it. Most ssllabs tests will show the intermediate cert not being sent. As long as you get the cert once, the browser won't have a problem again until the expiry date, if it isn't sent a cert.
I never had a problem loading the site (i.e., i received the cert), yet multiple tests at ssllabs (and elsewhere) showed one or both servers for the domain not sending the intermediate. So the problem will show up almost randomly.
The grade isn't particularly relevant, the actual tests are. You need to expand the results for each IP address. The Intermediate Certificate results at the bottom are the diagnostically significant results for this issue.
FF for Android may have received the cert, but it is also an entirely different beast than desktop FF. I don't know if it enforces the same policy strictness.
I do not know why the intermediate certificate would not be sent when on the same physical workstation another browser (Safari) has no complaint. FF will work sometimes then stop without closing the browser.
Can I interrogate or test the intermediate certificate manually ?
I believe I understand why other browser work. They go out to find the missing certificate where Firefox does not.
I agree with Firefox method as the problem is with the certificate and no browser should go seeking to correct for an error. Bravo FF
Can anyone tell me if Firefox shows the certificate chain?
Firefox caches intermediate certificates send by a server, so if you have visited a server that sends a specific intermediate certificate then you won't get an error if you visit a website that doesn't send the intermediate certificate (i.e. Firefox will fallback to the cached certificate).
วิธีแก้ปัญหาที่เลือก
If you click through to view the certificate from the taskbar, it shows the chain at the top of the cert window. Clicking each will show the referenced cert.
When using ssllabs.com, if you click one of the server addresses and scroll to the bottom of the report, it will also show you the chain and what is missing, if anything.
OK. Thanks