"Content-Type" header code execution
We are looking to find a fix for the code execution bug found in May of 2021:
Mozilla Firefox is vulnerable to code execution by a remote attacker who can convince a user to open a malicious file. By manipulating the "Content-Type" header of a file the attacker can cause Firefox to execute scripts concealed in files that appear to be of non-executable types.
被選擇的解決方法
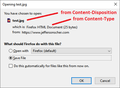
If you use my test document you will see that Firefox 96 still works the same way: when the server indicates this combination:
Content-Type: text/html Content-Disposition: attachment; filename=test.jpg
Firefox corrects the file name during the save process from test.jpg to test.jpg.html and you can open it as an HTML page rather than a corrupt JPEG image.
I don't know whether anyone has filed a bug. Normally security researchers would have done that before making a public disclosure but it is hard to search for security bugs.
If you want to file a new bug:
從原來的回覆中察看解決方案 👍 0所有回覆 (5)
Can you link to information about that vulnerability? To prevent a delay in your post appearing, add a space before the .com or .org in your link. (Otherwise, the reply is sent to the link spam moderation queue.)
I think this is what they're doing:
https://www.jeffersonscher.com/res/test_jpg.php
Adding screenshot of download dialog:

由 jscher2000 - Support Volunteer 於
That was the site I saw about this issue but no official notice or fix which is what is needed.
選擇的解決方法
If you use my test document you will see that Firefox 96 still works the same way: when the server indicates this combination:
Content-Type: text/html Content-Disposition: attachment; filename=test.jpg
Firefox corrects the file name during the save process from test.jpg to test.jpg.html and you can open it as an HTML page rather than a corrupt JPEG image.
I don't know whether anyone has filed a bug. Normally security researchers would have done that before making a public disclosure but it is hard to search for security bugs.
If you want to file a new bug: