Support ECH or ESNI in 128.2.0esr
Hello,
I installed Firefox 128.2.0esr. I set the next parameters in GPO for settings DNSOverHTTPS: "DNSOverHTTPS": {
"Enabled": true,
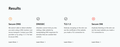
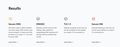
"ProviderURL": "https://safe.dot.dns.yandex.net/dns-query", "Locked": true, "Fallback": true }. But when checking via https://www.cloudflare.com/ru-ru/ssl/encrypted-sni/#results I get (screenshot in attachment). As you can see from the screenshot, DNS and SNI did not receive the coveted check marks. Secure DNS We weren’t able to detect whether you were using a DNS resolver over secure transport. Contact your DNS provider or try using 1.1.1.1 for fast & secure DNS. DNSSEC Attackers cannot trick you into visiting a fake website by manipulating DNS responses for domains that are outside their control. TLS 1.3 Nobody snooping on the wire can see the certificate of the website you made a TLS connection to. Secure SNI Anybody listening on the wire can see the exact website you made a TLS connection to.
In my browser / about:config: network.trr.mode = 2 network.trr.uri = https://safe.dot.dns.yandex.net/dns-query
In 128.2.0esr there is no protection against ESNI interceptions and ECH is enabled by default? Or is the problem that the DNS provider does not support the technology from Mozilla? Or what other settings we need use (via GPO)?
Thank you.
由 NoahSUMO 於
所有回覆 (1)
> Secure DNS We weren’t able to detect whether you were using a DNS resolver over secure transport. Contact your DNS provider or try using 1.1.1.1 for fast & secure DNS.
That just means you aren't using cloudflare's own DNS resolver over an encrypted connection. I get the same when using https://dns.google/dns-query as the DoH provider. The problem is that cloudflare can't know whether the connection between you and the recursive resolver is encrypted or not. I think this is expected behaviour.
> Anybody listening on the wire can see the exact website you made a TLS connection to.
It seems https://safe.dot.dns.yandex.net/dns-query doesn't return the correct ECH configs. Try using a different provider maybe?