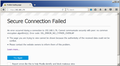
"Secure connection failed" SSL_ERROR_NO_CYPHER_OVERLAP, no "Advanced" button, v.50.1.0
After the automatic update to 50.1.0, I am no longer able to connect to https web interfaces of appliances on my LAN/VPN.
Before the update, I would receive a "Secure Connection Failed" page with an "Advanced" button that would allow me to confirm the security exception and continue to the web page.
Initially after the update, there was no "Advanced" option and the error code was SSL_ERROR_INAPPROPRIATE_FALLBACK_ALERT. As part of exploring solutions, I did a refresh of Firefox. After the refresh, the error code is now SSL_ERROR_NO_CYPHER_OVERLAP and there is still no "Advanced" button.
I can access the page via Internet Explorer after confirming a security exception. My OS is Windows 7 Home Premium Service Pack 1.
Επιλεγμένη λύση
The device is on the market today and is at the latest firmware version.
I have since tried Chrome, which does allow the security exception, but does not support the plugin required.
So IE it is then. Ugh.
Thanks for all your help.
Ανάγνωση απάντησης σε πλαίσιο 👍 0Όλες οι απαντήσεις (11)
Normally this error occurs on a website that is outdated in still supporting RC4 and having the security.tls.unrestricted_rc4_fallback preference toggled to false.
RC4 support has been completely removed in Firefox 50.0 and later as it is no longer able to be overridden. https://www.fxsitecompat.com/en-CA/docs/2016/rc4-support-has-been-completely-removed/ https://blog.mozilla.org/security/2015/09/11/deprecating-the-rc4-cipher/
Since you have Windows you could use the portable Firefox 45.6.0 ESR and enable the Preference just for this one thing that is insecure. The portable build can run on hdd or flash drive and will not touch your normal Firefox 50.1.0 install or Profile. http://portableapps.com/apps/internet/firefox-portable-esr
Τροποποιήθηκε στις
Many older devices have firmware updates to upgrade their SSL/TLS interfaces, but many do not. If yours falls into the category of being stuck in the past, unfortunately, you may no longer be able to manage it using Firefox. Have you already searched for updates?
Επιλεγμένη λύση
The device is on the market today and is at the latest firmware version.
I have since tried Chrome, which does allow the security exception, but does not support the plugin required.
So IE it is then. Ugh.
Thanks for all your help.
Please also complain to the manufacturer. Some users (Mac and Linux) do not even have IE as an option so they would be completely out of luck.
sangfroid said
The device is on the market today and is at the latest firmware version.
On the market as in still being manufactured or some stores still having them in stock.
What is the device model anyways?
What cipher suite and TLS version is Google Chrome using?
I have already submitted a request to Amcrest referencing this thread.
The product is an Amcrest Security Camera DVR (irony): Device Model:HCVR Record Channel:8 System Version:3.200.AC04.5, Build Date: 2015-09-16 Device Type:AMDV10808 Soft Version:10001 Device ID:Amcrest
================================================
Regarding Google Chrome: Version 55.0.2883.87 m Google Chrome is up to date.
https://cc.dcsec.uni-hannover.de/ reports:
SSL Cipher Suite Details of Your Browser
This websites gives you information on the SSL cipher suites your browser supports for securing HTTPS connections. Cipher Suites Supported by Your Browser (ordered by preference):
SpecCipher Suite NameKey SizeDescription (1a,1a)UnknownUnknown (cc,a9)UnknownUnknown (cc,a8)UnknownUnknown (cc,14)ECDHE-ECDSA-CHACHA20-POLY1305-SHA256128 BitKey exchange: ECDH, encryption: ChaCha20 Poly1305, MAC: SHA256. (cc,13)ECDHE-RSA-CHACHA20-POLY1305-SHA256128 BitKey exchange: ECDH, encryption: ChaCha20 Poly1305, MAC: SHA256. (c0,2b)ECDHE-ECDSA-AES128-GCM-SHA256128 BitKey exchange: ECDH, encryption: AES, MAC: SHA256. (c0,2f)ECDHE-RSA-AES128-GCM-SHA256128 BitKey exchange: ECDH, encryption: AES, MAC: SHA256. (c0,2c)ECDHE-ECDSA-AES256-GCM-SHA384256 BitKey exchange: ECDH, encryption: AES, MAC: SHA384. (c0,30)ECDHE-RSA-AES256-GCM-SHA384256 BitKey exchange: ECDH, encryption: AES, MAC: SHA384. (c0,09)ECDHE-ECDSA-AES128-SHA128 BitKey exchange: ECDH, encryption: AES, MAC: SHA1. (c0,13)ECDHE-RSA-AES128-SHA128 BitKey exchange: ECDH, encryption: AES, MAC: SHA1. (c0,0a)ECDHE-ECDSA-AES256-SHA256 BitKey exchange: ECDH, encryption: AES, MAC: SHA1. (c0,14)ECDHE-RSA-AES256-SHA256 BitKey exchange: ECDH, encryption: AES, MAC: SHA1. (00,9c)RSA-AES128-GCM-SHA256128 BitKey exchange: RSA, encryption: AES, MAC: SHA256. (00,9d)RSA-AES256-GCM-SHA384256 BitKey exchange: RSA, encryption: AES, MAC: SHA384. (00,2f)RSA-AES128-SHA128 BitKey exchange: RSA, encryption: AES, MAC: SHA1. (00,35)RSA-AES256-SHA256 BitKey exchange: RSA, encryption: AES, MAC: SHA1. (00,0a)RSA-3DES-EDE-SHA168 BitKey exchange: RSA, encryption: 3DES, MAC: SHA1.
Further information:
User-Agent:Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36 Preferred SSL/TLS version: TLSv1 SNI information: cc.dcsec.uni-hannover.de SSL stack current time: Tue, 28 May 1985 18:55:23
This connection uses TLSv1.2 with ECDHE-RSA-AES128-GCM-SHA256 and a 128 Bit key for encryption.
Raw:
Version: 3.1 Ciphers: 1a1a,cca9,cca8,cc14,cc13,c02b,c02f,c02c,c030,c009,c013,c00a,c014,9c,9d,2f,35,0a Extensions: 0a0a,ff01,0000,0017,0023,000d,0005,0012,0010,7550,000b,000a,fafa Remote Time: Tue, 28 May 1985 18:55:23
This service is provided by the DCSEC research group at Leibniz University Hannover. Imprint If you have any comments or questions please contact Sascha Fahl
Details from Chrome about the appliance page:
Security Overview This page is insecure (broken HTTPS).
Certificate Error There are issues with the site's certificate chain (net::ERR_CERT_AUTHORITY_INVALID).
SHA-1 Certificate The certificate for this site expires in 2016, and the certificate chain contains a certificate signed using SHA-1. Secure Resources All resources on this page are served securely.
Obsolete Connection Settings The connection to this site uses a strong protocol (TLS 1.2), an obsolete key exchange (RSA), and a strong cipher (AES_128_GCM).
Certificate:
Version: V3 Serial Number: ?30 30 65 30 34 63 36 38 30 34 66 37 31 34 32 37 34 34 34 39 30 35 Signature algorithm: sha1RSA Signature hash algorithm: sha1 Issurer: O = Amcrest Technologies LLC L = Houston S = Taxas C = US CN = Product Root CA Valid from: ?Thursday, ?March ?26, ?2015 12:28:25 AM Valid to: ?Saturday, ?March ?26, ?2016 12:28:25 AM Subject: O = Amcrest Technologies LLC L = Houston S = Taxas C = US CN = 192.168.1.108 Public key: RA (1024 Bits) Subject Key Identifier: ac 28 85 02 fc 07 d8 d0 18 02 f5 35 27 ec ec 03 ed af 62 eb Basic Constraints: Subject Type=End Entity Path Length Constraint=None Thumbprint algorithm: sha1 Thumbprint: ?a8 72 7b 58 b7 08 f7 34 4e 12 a5 bd 68 e4 79 a1 56 97 5d 90
sangfroid said
Details from Chrome about the appliance page:
Security Overview This page is insecure (broken HTTPS).
Certificate Error There are issues with the site's certificate chain (net::ERR_CERT_AUTHORITY_INVALID).
SHA-1 Certificate The certificate for this site expires in 2016, and the certificate chain contains a certificate signed using SHA-1.
Secure Resources All resources on this page are served securely.
Obsolete Connection Settings The connection to this site uses a strong protocol (TLS 1.2), an obsolete key exchange (RSA), and a strong cipher (AES_128_GCM).
Let's start with that issue about the key exchange, and check on your settings in general.
(1) In a new tab, type or paste about:config in the address bar and press Enter/Return. Click the button promising to be careful.
(2) In the search box above the list, type or paste TLS and pause while the list is filtered
(3) If you have any non-default settings (typically bolded and having a status of "user set"), you can make a note of the values in case they turn out to be important for some other reason, then right-click > Reset each prefer to its default value.
If you have any locked preferences (typically italicized), you may have an external lock file modifying your Firefox configuration.
(4) In the search box above the list, type or paste security.ss and pause while the list is filtered
(5) If you have any non-default settings (typically bolded and having a status of "user set"), you can make a note of the values in case they turn out to be important for some other reason, then right-click > Reset each prefer to its default value.
However: Please double-click each of these to switch them from true to false (this works around any servers that have not yet been fixed for the Logjam vulnerability):
- security.ssl3.dhe_rsa_aes_128_sha => false
- security.ssl3.dhe_rsa_aes_256_sha => false
Again, if you have any locked preferences (typically italicized), you may have an external lock file modifying your Firefox configuration.
Then if you reload the router's page again, do you get the other error page with the Advanced button?
Sorry, I have tried many workarounds including this. It gives the same page.
I regard the answers above as complete, and will mark using a different browser as 'solved', so that other users may realize that Firefox has moved beyond them.
Again, thank you all for the help.
Quote: ECDHE-RSA-AES128-GCM-SHA256
That looks like cipher suite:
- security.ssl3.ecdhe_rsa_aes_128_gcm_sha256
Try to enable only this cipher suite and disable all the others in case there is a problem with the cipher order that Firefox tries.
When all other security.ssl3.* settings, except
- security.ssl3.ecdhe_rsa_aes_128_gcm_sha256
are set, the connection fails with the same message and no "Advanced" button.
Further, I swept the security.ssl3.* settings, enabling only one at a time. Same response in each case as expected, based on James' response above.