BTinternet SSL/TLS no longer works but no change was made to Thunderbird, any ideas please?
For several years I have been using Mozilla Thunderbird as my e-mail client to BT e-mail.
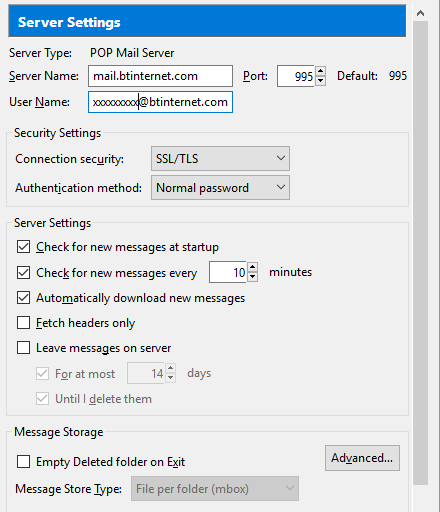
I have connected via pop3.btinternet.com:995 with SSL/TLS set.
In the last few days this no longer works, but no changes had been made to my settings. The same problem occurs on a totally separate laptop connected to the same BT router.
I have had to change to insecure sign in on Port 110.
I have corresponded with the BT help desk, but they claim no known problems and have suggested I contact Thunderbird help for a solution.
All Replies (15)
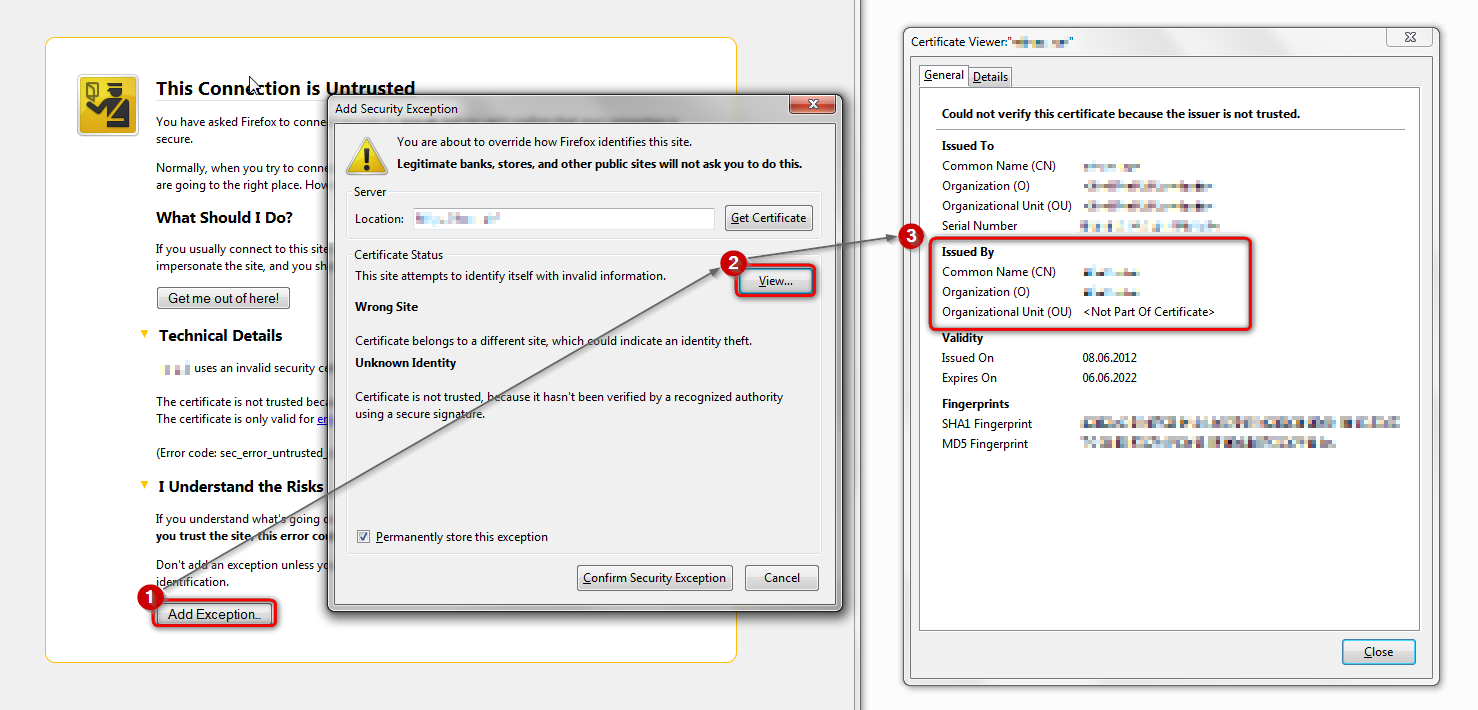
Inspect the certificate - see attached screenshot for instructions.
Who is the issuer of the cert? What's the subject field of the cert?
Please post a screenshot of the Certificate Viewer window with the information above visible.
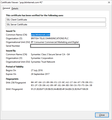
Please see the extracts from the certificate viewer attached
What about the expiry date? what fingerprints does it offer?
The expiry date was sometime in 2019.
Sorry but I was not inclined to publish the fingerprints, as I suspect that would allow anybody to hack the account, but please excuse my ignorance on this subject.
I have since re-set my password on the BTinternet server and obtained a new certificate and have successfully received e-mails with SSL/TLS enabled.
Many thanks to christ1 and to Matt for their interest in my problem. On-line security is becoming a mysterious subject and it is not clear where to get the best advice.
What's the subject field of the cert?
It may not have been obvious, but that meant the 'Issued To' part of the cert, which wasn't visible in your screenshots.
I have since re-set my password on the BTinternet server and obtained a new certificate
I'd really be curious what cert you 'obtained'. Do you use a client cert instead of a password to authenticate to the server? Most likely not. That means you wouldn't have a cert at all. It's the server sending the cert to the email client. Unless BT just renewed their server cert, that cert shouldn't change until it get's renewed by BT. If you received a different cert last time, that could be a very bad sign.
On-line security is becoming a mysterious subject
It isn't mysterious at all, but it indeed requires a little knowledge, which unfortunately only few people seems to have.
I was not inclined to publish the fingerprints, I suspect that would allow anybody to hack the account,
The fingerprint is used to unambiguously identify a cert. The cert itself is public knowledge, and you wouldn't reveal any sensitive information.
Is this the cert you get?
openssl s_client -connect pop3.btinternet.com:995 CONNECTED(00000003) depth=2 C = US, O = "VeriSign, Inc.", OU = VeriSign Trust Network, OU = "(c) 2006 VeriSign, Inc. - For authorized use only", CN = VeriSign Class 3 Public Primary Certification Authority - G5 verify return:1 depth=1 C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 Secure Server CA - G4 verify return:1 depth=0 C = GB, ST = London, L = London, O = BRITISH TELECOMMUNICATIONS PLC, CN = pop.btinternet.com verify return:1 --- Certificate chain 0 s:/C=GB/ST=London/L=London/O=BRITISH TELECOMMUNICATIONS PLC/CN=pop.btinternet.com i:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 Secure Server CA - G4 1 s:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 Secure Server CA - G4 i:/C=US/O=VeriSign, Inc./OU=VeriSign Trust Network/OU=(c) 2006 VeriSign, Inc. - For authorized use only/CN=VeriSign Class 3 Public Primary Certification Authority - G5
Then there's a mismatch with the certs common name (CN) with the name of the server the cert has been issued for:
pop.btinternet.com vs. pop3.btinternet.com
This is what Thunderbird is complaining about, and you should be complaining to BT.
Modified
Since I have apparently 'fixed' the problem I am unable to find out how to view the current certificate. I would be grateful for your advice on this.
The exception was caused whenever I attempted to "Get Messages" and then I had the "Add Security Exception" dialogue which included the View button for the Certificate Status.
For information, I have disabled the account I was having trouble with, particularly because the exception message re-appeared.
I have now created a new account by providing Thunderbird with my e-mail address and password and connected via POP3.
Thunderbird has now connected to the server mail.btinternet.com (See image).
I hope this resolves the matter, but would appreciate any further advice that might be offered on the subject.
Many thanks.
Given the seemingly twice (or thrice) change in certs and the discrepancy mentioned and shown by christ1, I'd be VERY LEARY of doing anything sensitive or critical with btinternet until THEY explain the cert shuffling and such. Again, as Christ1 mentioned the Thunderbird application is doing its job of saying 'Hello there, you look like odd/suspect, let's have this checked out.' pop to pop3 should surely not been an unannounced change and would have warranted a cert change, and acknowledgment from BTinternet of the same.
Thanks Corey, I did contact BTinternet. The support desk lady was not a great deal of help frankly, but suggested I contact the Thunderbird help team.
Most of my e-mail traffic is social, so hopefully not too sensitive or critical.
I have just written to customer.care@bt.com in the hope that they might investigate further.
BT email is actually yahoo. Enough said?
It was changing over to an outfit called CriticalPath but that changeover appears to have fizzled out.
Since I have apparently 'fixed' the problem I am unable to find out how to view the current certificate.
Good point. Basically when Thunderbird isn't complaining, you can sort of assume that there's no major problem.
I'm not aware of any way to check the cert from within Thunderbird. Outside of Thunderbird, one way would be to use openssl to retrieve the cert.
openssl s_client -connect mail.btinternet.com:995 CONNECTED(00000003) depth=2 C = US, O = "VeriSign, Inc.", OU = VeriSign Trust Network, OU = "(c) 2006 VeriSign, Inc. - For authorized use only", CN = VeriSign Class 3 Public Primary Certification Authority - G5 verify return:1 depth=1 C = US, O = Symantec Corporation, OU = Symantec Trust Network, CN = Symantec Class 3 Secure Server CA - G4 verify return:1 depth=0 C = GB, ST = LONDON, L = LONDON, O = BRITISH TELECOMMUNICATIONS PLC, OU = BT Consumer Commercial Marketing and Digital, CN = mail.btinternet.com verify return:1 --- Certificate chain 0 s:/C=GB/ST=LONDON/L=LONDON/O=BRITISH TELECOMMUNICATIONS PLC/OU=BT Consumer Commercial Marketing and Digital/CN=mail.btinternet.com i:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 Secure Server CA - G4 1 s:/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 Secure Server CA - G4 i:/C=US/O=VeriSign, Inc./OU=VeriSign Trust Network/OU=(c) 2006 VeriSign, Inc. - For authorized use only/CN=VeriSign Class 3 Public Primary Certification Authority - G5 --- Server certificate
BEGIN CERTIFICATE----- MIIGpDCCBYygAwIBAgIQTE0Ei52sJ1Lne7xHYXJjwTANBgkqhkiG9w0BAQsFADB+ MQswCQYDVQQGEwJVUzEdMBsGA1UEChMUU3ltYW50ZWMgQ29ycG9yYXRpb24xHzAd BgNVBAsTFlN5bWFudGVjIFRydXN0IE5ldHdvcmsxLzAtBgNVBAMTJlN5bWFudGVj IENsYXNzIDMgU2VjdXJlIFNlcnZlciBDQSAtIEc0MB4XDTE3MDYxNDAwMDAwMFoX DTE5MDgxMzIzNTk1OVowga0xCzAJBgNVBAYTAkdCMQ8wDQYDVQQIDAZMT05ET04x DzANBgNVBAcMBkxPTkRPTjEnMCUGA1UECgweQlJJVElTSCBURUxFQ09NTVVOSUNB VElPTlMgUExDMTUwMwYDVQQLDCxCVCBDb25zdW1lciBDb21tZXJjaWFsIE1hcmtl dGluZyBhbmQgRGlnaXRhbDEcMBoGA1UEAwwTbWFpbC5idGludGVybmV0LmNvbTCC ASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMtAa80QYTeAy4OEc0XRh22y 6VrvMVz5/kx9tG7mGmVyFdWLkFbxHOy4E8ZSpFsKE9bElKwaw1rjRfblcEIq4xIv +jbKrNq6LdcKZiZNQnhRSf5D8TyyGVwt9XHxZHOsdetz34UEanKM9OIyyR8Ybagk aqOKSnWdGAhBgrnCkB3Sl7HJpha0w3W3FrlZcujfI3GzpM7Odq5IGwkZkKsdh3/+ sey7fbN6i8bnW96nuW05tyQLhKPUFOzgjMu4MUBsweKbMoHfZCChVRU2o4Wg234T zI1nX+ewXyJKw8Flz+puFBvJo7xLWVy+HHt6lSKlDkd9KcNOVoQb5KkHjwh45eEC AwEAAaOCAuwwggLoMB4GA1UdEQQXMBWCE21haWwuYnRpbnRlcm5ldC5jb20wCQYD VR0TBAIwADAOBgNVHQ8BAf8EBAMCBaAwYQYDVR0gBFowWDBWBgZngQwBAgIwTDAj BggrBgEFBQcCARYXaHR0cHM6Ly9kLnN5bWNiLmNvbS9jcHMwJQYIKwYBBQUHAgIw GQwXaHR0cHM6Ly9kLnN5bWNiLmNvbS9ycGEwKwYDVR0fBCQwIjAgoB6gHIYaaHR0 cDovL3NzLnN5bWNiLmNvbS9zcy5jcmwwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsG AQUFBwMCMB8GA1UdIwQYMBaAFF9gz2GQVd+EQxSKYCqy9Xr0QxjvMFcGCCsGAQUF BwEBBEswSTAfBggrBgEFBQcwAYYTaHR0cDovL3NzLnN5bWNkLmNvbTAmBggrBgEF BQcwAoYaaHR0cDovL3NzLnN5bWNiLmNvbS9zcy5jcnQwggGABgorBgEEAdZ5AgQC BIIBcASCAWwBagB3AN3rHSt6DU+mIIuBrYFocH4ujp0B1VyIjT0RxM227L7MAAAB XKZHPgEAAAQDAEgwRgIhAJemDfmT4TBh875HenMXB5mFb2NgVjYmaPhVNdRq/nqD AiEA/M0EVCwi9wFJ/WgDsShdRNGkVU2jmQUoI6a7OIDTFesAdgCkuQmQtBhYFIe7 E6LMZ3AKPDWYBPkb37jjd80OyA3cEAAAAVymRz4WAAAEAwBHMEUCIGIgpoUCsjfH FzJ+miPPJ6Bhu8dmI8iRzgI+z7mrlfNnAiEAthjl5Z3ZXnSQ8ATf8VHQhsEE109C P3h1MjON3n97C4UAdwDuS723dc5guuFCaR+r4Z5mow9+X7By2IMAxHuJeqj9ywAA AVymR0AAAAAEAwBIMEYCIQCMWbdop5h7WV5xapsvf8dmpTbf6IW3LlWxguP72BY6 0AIhAP27r0jMvJ6aM09b9EEz4fAnSdlbuUr9P1pMldP6esDrMA0GCSqGSIb3DQEB CwUAA4IBAQCFpLMp6lAbA9B9BYQb8Rnya+tAnt28Pa+DWZEYp6EyxXrcYhnh7A+l Dhdzrl28bQEv9yXjg7h1fui7hMKhBvL0YXTjG/XhSfav5UCczPP/8D0I38KT/sKP csmINSKOiGOdQdPZ9cuq6MSj+f2uQt7aASMbD4YiarqhEghDXXkgx8SJeOWe0tWH jQ2WulekMNmNGAFUK7Z+ehdV9RDaWPZjqHSPXxoPBB4nkgtm09KISSK6NGxSxTVd 4/5+pidcyzmxRLwHHtGOFM3X4O2zfHvQOdZneGv13jn0Exs2gpVwlWDGreXtltGg Vlk/AWwrLM87cBUXKnCH3PG4xGx87Sia
END CERTIFICATE----- subject=/C=GB/ST=LONDON/L=LONDON/O=BRITISH TELECOMMUNICATIONS PLC/OU=BT Consumer Commercial Marketing and Digital/CN=mail.btinternet.com issuer=/C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 Secure Server CA - G4 --- No client certificate CA names sent --- SSL handshake has read 3222 bytes and written 635 bytes --- New, TLSv1/SSLv3, Cipher is AES256-SHA Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : AES256-SHA Session-ID: 409A724A730AD979B0A544A40AA3E604C8A8AEEFFB87F3AA95698F9E8E2A11F6 Session-ID-ctx: Master-Key: 25DA0267B84031B731F950B485104CD5090FE389907F5460118F4B03E3DD82CE0FF64EBEF8E7465361B148D64825A77A Key-Arg : None PSK identity: None PSK identity hint: None SRP username: None Start Time: 1506016769 Timeout : 300 (sec) Verify return code: 0 (ok) --- DONE
Mine stopped working and having cleared it and set it up again, it's now working and the settings Thunderbird has found are as follows:
account44:
INCOMING: account44, , (imap) mail.btinternet.com:993, SSL, passwordCleartext
OUTGOING: , mail.btinternet.com:465, SSL, passwordCleartext, true
And I stand corrected; it is now using CriticalPath and not Yahoo:
Source TTL Address Type Record Type Resolution
mail.btinternet.com. 49318 IN CNAME mail.btinternet.bt.lon5.cpcloud.co.uk.
mail.btinternet.bt.lon5.cpcloud.co.uk. 137 IN A 65.20.0.43
So we can check who owns that last IP address:
#
# The following results may also be obtained via:
# https://whois.arin.net/rest/nets;q=65.20.0.43?showDetails=true&showARIN=false&showNonArinTopLevelNet=false&ext=netref2
#
NetRange: 65.20.0.0 - 65.21.255.255
CIDR: 65.20.0.0/15
...
Organization: Critical Path Inc. (CPAT)
RegDate: 2001-01-29
Updated: 2012-11-28
Ref: https://whois.arin.net/rest/net/NET-65-20-0-0-1
To the OP: if you're using IMAP, it isn't very much effort to delete and re-install the account. This gives Thunderbird an opportunity to refresh the settings. You get all your messages back in a trice.
Of course filters and anything else that refers to account folder names might require attention to bring them up to date and into line with the new configuration.
christ1 wrote: I'm not aware of any way to check the cert from within Thunderbird. Outside of Thunderbird, one way would be to use openssl to retrieve the cert.
I eventually found it:
Account Settings > Security > Manage Certificates
Select an 'appropriate' certificate > View
I note that it expires on 26th September 2017 (in four days time), so I expect I will have more of this problem.
Modified
[ How do you do that neat highlighting ?]
The formatting doesn't seem to allow to insert the raw tags. Inspect the page source and look for 'blockquote' tags.
I note that it expires on 26th September 2017 (in four days time), so I expect I will have more of this problem.
It is common practice not to wait until the last minute before expiry to renew a cert. I suppose this is what BT did.
Modified