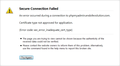
Getting sec_error_inadequate_cert_type with Private SSL Cert
Howdy,
I run a Private Certificate Authority for my personal use and just to learn about SSL Certs. However, with the current build of FireFox I'm on ( 31 ) I can no longer visit sites I've secured with SSL Certs signed by this certificate authority, even though these SSL certs work just perfectly fine in Chrome and Internet Explorer. I keep getting a "sec_error_inadequate_cert_type" error. I can only assume that the certs I've been issuing are incorrect in some way, but the error is so vague and the error page doesn't specify more.
I only discovered this when I realized some of my SSL certs had expired, and I went to re-issue them.
One of the certs that hasn't expired yet but is experiencing problems can be found here:
One of the Certs I've tried re-issuing, matching fields included as closely as I can to a Google SSL cert that I looked up is here:
These certificates were generated using the application called SimpleAuthority, found here: http://simpleauthority.com/
A Site like Networking4All.com seems to believe the Certs are valid, excepting the CA that is Self Signed: http://www.networking4all.com/en/support/tools/site+check/report/?fqdn=phpmyadmin.endofevolution.com&protocol=https
Interestingly enough, using a different site like SSLShopper shows an error similar to FF31: http://www.sslshopper.com/ssl-checker.html#hostname=https://phpmyadmin.endofevolution.com
The certs are running on an Apache Web server: Apache/2.2.21 (Win32) mod_ssl/2.2.21 OpenSSL/1.0.0e PHP/5.3.10
The CA Cert is in FireFox's store as trusted.
If needed, I can provide certs.
Mafitar da aka zaɓa
I discovered the problem: The CA Certificate I was using had extended usage included.
Refer to Bug: 1049176
I confirmed this by generating a new test CA with the the extended usage field excluded, then generating a new SSL Cert The certificate verifies properly now.
While I am relieved I have figured out what the problem is, being so vague with the error message is making me lean towards another browser for primary usage. The fact it took me 4 days and an extremely large amount of work to figure out why this was occurring was unacceptable, all because the error description was generic and included absolutely no details what so ever.
Karanta wannan amsa a matsayinta 👍 2All Replies (6)
I get this error in Google Chrome as well.
Current Firefox releases no longer allow to add an exception with the switch to PKIX. You would have to disable PKIX temporarily when visiting a site that doesn't work with it.
- Bug 1034124 - mozilla::pkix: the error encountered when a CA certificate is used as an end-entity is not overridable
Note that you won't be able to do this with the next 33 Firefox version as support for this pref has been removed.
- Bug 975229 - Remove NSS-based certificate verification
There are more changes to certificates, see:
An gyara
I however, do not. It's something specific to Firefox I seem to be having. Maybe I'm running an outdated version of Chrome? Which would be hard seeing as chrome itself says it's up to date: Version 37.0.2062.120 m
I appreciate the link to Bug 1034124, However the SSL certificate itself IS NOT self signed. Only the CA is, which signed the SSL Cert. I guess what I mean to be asking is... Is Firefox Rejecting my SSL Cert, because my CA Is Self Signed?
I also offer the CA Cert for download since no one would have the cert in their stores. Would this also affect it?
I've attached a screen shot of the error I'm getting so that it's available for the ticket. The following is also the "plaintext" verison of the error I'm getting:
"Certificate type not approved for application."
I finally found a tool online that will show me the guts of the certificate: http://certlogik.com/ssl-checker/phpmyadmin.endofevolution.com/
Everything seems to be good...
Zaɓi Mafita
I discovered the problem: The CA Certificate I was using had extended usage included.
Refer to Bug: 1049176
I confirmed this by generating a new test CA with the the extended usage field excluded, then generating a new SSL Cert The certificate verifies properly now.
While I am relieved I have figured out what the problem is, being so vague with the error message is making me lean towards another browser for primary usage. The fact it took me 4 days and an extremely large amount of work to figure out why this was occurring was unacceptable, all because the error description was generic and included absolutely no details what so ever.
SniperFodder said
I however, do not. It's something specific to Firefox I seem to be having. Maybe I'm running an outdated version of Chrome? Which would be hard seeing as chrome itself says it's up to date: Version 37.0.2062.120 m I appreciate the link to Bug 1034124, However the SSL certificate itself IS NOT self signed. Only the CA is, which signed the SSL Cert. I guess what I mean to be asking is... Is Firefox Rejecting my SSL Cert, because my CA Is Self Signed? I also offer the CA Cert for download since no one would have the cert in their stores. Would this also affect it? I've attached a screen shot of the error I'm getting so that it's available for the ticket. The following is also the "plaintext" verison of the error I'm getting: "Certificate type not approved for application."
I had the same issue, what i did was, copy two cert from your computer 1 is trusted rootCA cert 2.root CA1 from mmc console save those two cert into local computer then import it into mozilla firefox, under options->Advanced-> Certificates->view certificate->authorities->import-> restart it should work
An gyara