wierd SSL_ERROR_BAD_CERT_DOMAIN on wildcard domain
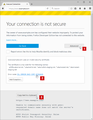
I get the error: SSL_ERROR_BAD_CERT_DOMAIN on my wildcard certificate, but according to the details text I believe it should be correct:
"sub.example.td1 uses an invalid security certificate. The certificate is only valid for the following names: example.td2, *.example.td2, *.*.example.td2, *.*.*.example.td2, example.td1, *.example.td1, *.*.example.td1, *.*.*.example.td1"
All Replies (18)
- uses an invalid security certificate SSL_ERROR_BAD_CERT_DOMAIN
- configured their website improperly
How to troubleshoot the error code "SEC_ERROR_UNKNOWN_ISSUER" on secure websites
https://support.mozilla.org/en-US/kb/troubleshoot-SEC_ERROR_UNKNOWN_ISSUER
Endret
FredMcD said
How to troubleshoot the error code "SEC_ERROR_UNKNOWN_ISSUER" on secure websites https://support.cdn.mozilla.net/media/uploads/images/thumbnails/2017-06-07-08-34-22-cb6da3.png https://support.mozilla.org/en-US/kb/troubleshoot-SEC_ERROR_UNKNOWN_ISSUER
- uses an invalid security certificate SSL_ERROR_BAD_CERT_DOMAIN
- configured their website improperly
I have already added the CA to my list of trust, so it's NOT a UNKNOWN_ISSUER,
What further detail do you see if you click the blue error code (screenshot)?
cor-el said
What further detail do you see if you click the blue error code (screenshot)?
"Unable to communicate securely with peer: requested domain name does not match the server’s certificate.
HTTP Strict Transport Security: false HTTP Public Key Pinning: false
Certificate chain:
**"
and here is the filtered cert in text format(openssl x509 -in test.der -noout -text): "Certificate:
Data:
Version: 3 (0x2)
Serial Number: 4727 (0x1277)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=NA, ST=NA, O=example, OU=example Certificate Authority, CN=example Intermediate CA
Validity
Not Before: Sep 20 20:54:07 2017 GMT
Not After : Sep 30 20:54:07 2018 GMT
Subject: C=NA, ST=NA, O=example, OU=Web, CN=example.td1
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
**
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Cert Type:
SSL Server
Netscape Comment:
OpenSSL Generated Server Certificate
X509v3 Subject Key Identifier:
8D:5F:B9:38:A2:93:AA:D3:AC:49:5E:88:9F:1A:0E:DC:B9:56:71:86
X509v3 Authority Key Identifier:
keyid:BC:0D:73:0C:9F:0E:AD:D0:D9:B0:E1:09:6C:5B:BB:CA:27:64:21:F3
DirName:/C=NA/ST=NA/O=example/OU=example Certificate Authority/CN=example Root CA
serial:12:53
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 CRL Distribution Points:
Full Name:
URI:http://ca.example.td1/ICA.crl
X509v3 Subject Alternative Name:
DNS:example.td2, DNS:*.example.td2, DNS:*.*.example.td2, DNS:*.*.*.example.td2, DNS:example.td1, DNS:*.example.td1, DNS:*.*.example.td1, DNS:*.*.*.example.td1
Signature Algorithm: sha256WithRSAEncryption
**"
Endret
Avalitan said
sub.example.td1 uses an invalid security certificate.
The certificate is only valid for the following names: example.td2, *.example.td2, *.*.example.td2, *.*.*.example.td2, example.td1, *.example.td1, *.*.example.td1, *.*.*.example.td1
Is sub.example.td1 the only domain you've found that seems to match the SAN list (*.example.td1) that does not work, or is there a problem with other domains on the list?
Does it pass a test such as: https://www.ssllabs.com/ssltest/ (assumes the site is accessible from the web)
jscher2000 said
Avalitan saidsub.example.td1 uses an invalid security certificate.
The certificate is only valid for the following names: example.td2, *.example.td2, *.*.example.td2, *.*.*.example.td2, example.td1, *.example.td1, *.*.example.td1, *.*.*.example.td1Is sub.example.td1 the only domain you've found that seems to match the SAN list (*.example.td1) that does not work, or is there a problem with other domains on the list?
Does it pass a test such as: https://www.ssllabs.com/ssltest/ (assumes the site is accessible from the web)
The same problem happens if I use .td2, it works fine on chrome.
according to ssllabs: "If trust issues are ignored: B", but it's a private CA, witch I have added to both Windows & Firefox, so there is no trust chain issues. Other than that there does not seem to be any problems. Firefox 53 / Win 7 is OK
Here is the root CA in text format: "Certificate:
Data:
Version: 3 (0x2)
Serial Number: 14108432359054352392 (0xc3cb387b1b0fa008)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=NA, ST=NA, O=example, OU=example Certificate Authority, CN=example Root CA
Validity
Not Before: Sep 7 15:25:35 2015 GMT
Not After : Dec 31 15:25:35 2120 GMT
Subject: C=NA, ST=NA, O=example, OU=example Certificate Authority, CN=example Root CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (8192 bit)
Modulus:
**
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
D5:6C:E2:87:8F:24:B2:E2:FA:D5:BB:6C:53:E0:8A:DD:10:E0:2C:5D
X509v3 Authority Key Identifier:
keyid:D5:6C:E2:87:8F:24:B2:E2:FA:D5:BB:6C:53:E0:8A:DD:10:E0:2C:5D
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Key Usage: critical
Digital Signature, Certificate Sign, CRL Sign
Signature Algorithm: sha256WithRSAEncryption
**"
In case it's some obscure legacy setting we're not thinking of, could you:
New Profile Test
This takes about 3 minutes, plus the time to test your site.
Inside Firefox, type or paste about:profiles in the address bar and press Enter/Return to load it.
Click the Create a New Profile button, then click Next. Assign a name like Sept2017, ignore the option to relocate the profile folder, and click the Finish button.
After creating the profile, scroll down to it and click the Set as default profile button below that profile, then scroll back up and click the Restart normally button. (There are some other buttons, but I think those are still "under construction" so please ignore them.)
Firefox should exit and then start up using the new profile, which will just look brand new.
Does Firefox handle the certificate any better in the new profile?
When you are done with the experiment, open the about:profiles page again, click the Set as default profile button for your normal profile, then click the Restart normally button to get back to it.
jscher2000 said
In case it's some obscure legacy setting we're not thinking of, could you: New Profile Test This takes about 3 minutes, plus the time to test your site. Inside Firefox, type or paste about:profiles in the address bar and press Enter/Return to load it. Click the Create a New Profile button, then click Next. Assign a name like Sept2017, ignore the option to relocate the profile folder, and click the Finish button. After creating the profile, scroll down to it and click the Set as default profile button below that profile, then scroll back up and click the Restart normally button. (There are some other buttons, but I think those are still "under construction" so please ignore them.) Firefox should exit and then start up using the new profile, which will just look brand new. Does Firefox handle the certificate any better in the new profile? When you are done with the experiment, open the about:profiles page again, click the Set as default profile button for your normal profile, then click the Restart normally button to get back to it.
Same problem in the new profile.
Please provide public link(s) (no password) that we can check out. No Personal Information Please !
FredMcD said
Please provide public link(s) (no password) that we can check out. No Personal Information Please !
CA cert: https://1.ca.avalitan.com/ca.crt Sites: https://sub.avalitan.moe/ https://sub.avalitan.com/
https://sub.avalitan.moe/
sub.avalitan.moe uses an invalid security certificate. The certificate is not trusted because the issuer certificate is unknown. The server might not be sending the appropriate intermediate certificates. An additional root certificate may need to be imported. The certificate is only valid for the following names:
avalitan.com, *.avalitan.com, *.*.avalitan.com, *.*.*.avalitan.com, avalitan.moe, *.avalitan.moe, *.*.avalitan.moe, *.*.*.avalitan.moe
Error code: SEC_ERROR_UNKNOWN_ISSUER
sub.avalitan.com uses an invalid security certificate. The certificate is not trusted because the issuer certificate is unknown. The server might not be sending the appropriate intermediate certificates. An additional root certificate may need to be imported. Error code: SEC_ERROR_UNKNOWN_ISSUER
FredMcD said
https://sub.avalitan.com/ sub.avalitan.com uses an invalid security certificate. The certificate is not trusted because the issuer certificate is unknown. The server might not be sending the appropriate intermediate certificates. An additional root certificate may need to be imported. Error code: SEC_ERROR_UNKNOWN_ISSUER
the first link(to ca.crt) is the root certificate, and SEC_ERROR_UNKNOWN_ISSUER is because the root certificate is not installed, With the root certificate(https://1.ca.avalitan.com/ca.crt) installed I get the error: SSL_ERROR_BAD_CERT_DOMAIN.
Endret
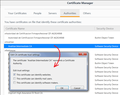
Okay, I imported the signing certificate as a trusted authority (see attached screenshot).
I used this method: click the Add Exception button, in the dialog click the View button, in the Certificate viewer click the Details tab, select the signing certificate one level up from the site certificate and click Export, use the default .crt format. Then in Options, Advanced, Certificates, click Certificate Manager, click the Authorities tab, click the Import button, and import the file you exported, then check the first box to trust the cert for websites.
After that, I get a nice green padlock on https://sub.avalitan.com/ (Firefox 55.0.3).
But I get the bad cert domain error for https://sub.avalitan.moe/ which is strange because it is on the SAN list. This matches your original post as its the second TLD in the set.
A search related to wildcard certs only turned up the following, which dates way back to Firefox 37: https://www.fxsitecompat.com/en-CA/docs/2015/certs-with-an-absolute-dns-id-or-irregular-wildcard-are-no-longer-supported/
Is this a new issue in your experience or did not you test this in previous versions of Firefox?
Endret
If you wanted to test Firefox 36, you can use the "Portable" edition, which installs into a folder and doesn't touch your main Firefox folders.